By Tyler Greenwood, Vice President of Back To Business I.T. (originally published in the Dayton Business Journal)
Cyber incidents like the SolarWinds attack in 2019 and the Colonial Pipeline ransomware attack in 2021 have the U.S. Department of Defense (DoD) taking urgent action to strengthen national cybersecurity regulations.
A report released last November found most prime contractors (and their subcontractors) hired by the DoD in the last five years failed to meet minimum cybersecurity standards, putting U.S. national security at risk. Security gaps in the federal supply chain have been well known for years, but attempts to fix them have failed.
Enter: CMMC
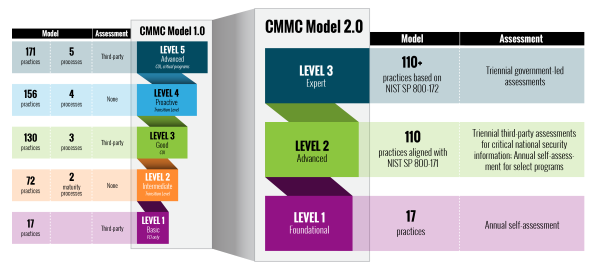
In response to heightened security risks, the DoD introduced Cybersecurity Maturity Model Certification (CMMC) program. Its goal is to ensure any company involved in the federal supply chain is protecting controlled unclassified information.
Under CMMC guidelines, more than 300,000 contractors must meet 110 NIST SP 800-171 controls, which the government sees as a reasonable cyber risk management approach. In addition, 80,000 of these organizations must complete a third-party assessment and certification to continue bidding on defense contracts.
When will CMMC certification be required?
The DoD is expected to release a final rule on CMMC framework by March 2023, which means contractors could start seeing requirements in RFPs/RFIs as early as May.
If your business is one of the 80,000 contractors that requires an outside assessment and certification, you may have less than a few months to do so. Failure to achieve compliance before the published rule could mean leaving money on the table and losing the ability to do business with the Department of Defense.
Getting started
If your company is still in the beginning stages of CMMC compliance, the time to act is now. Preparation and implementation of the following requirements can take upwards of 18 months. To get started on compliance, contractors should immediately:
- Work toward meeting the 110 controls in NIST SP 800-171.
- Identify their Supplier Performance Risk System (SPRS) score.
- Create a system security plan (SSP).
- Document plans of action and milestones (POA&M) to demonstrate how you intend to close any gaps for controls not yet met.
Next steps
If your organization has already started on CMMC compliance, consider conducting a preliminary self-assessment to see if you satisfy requirements. This can provide a range of helpful information to ensure you have everything functioning as expected once you’re ready to formally self-attest or go for your official certification.
If your business wants consultative guidance, including assistance walking you through standards you didn’t meet, explaining why, and offering suggestions on closing those gaps, you might find it beneficial to work with a CMMC Registered Provider Organization (RPO), such as Back To Business I.T.
As a full-service I.T. firm and the region’s leading CMMC-AB RPO, Back To Business I.T. can help you achieve NIST SP 800-171 compliance as well as help you prepare your plan of action and milestones (POA&M) and system security plan (SSP) required for CMMC certification. Learn more at www.backtobusinessit.com/cmmc-readiness.